This week I learned about Bazar Call /Bazarloader Malware. I had never heard of this malware campaign. Even when it was explained to me I didn’t think that it would have a high success rate, but doing more research it is really successful.
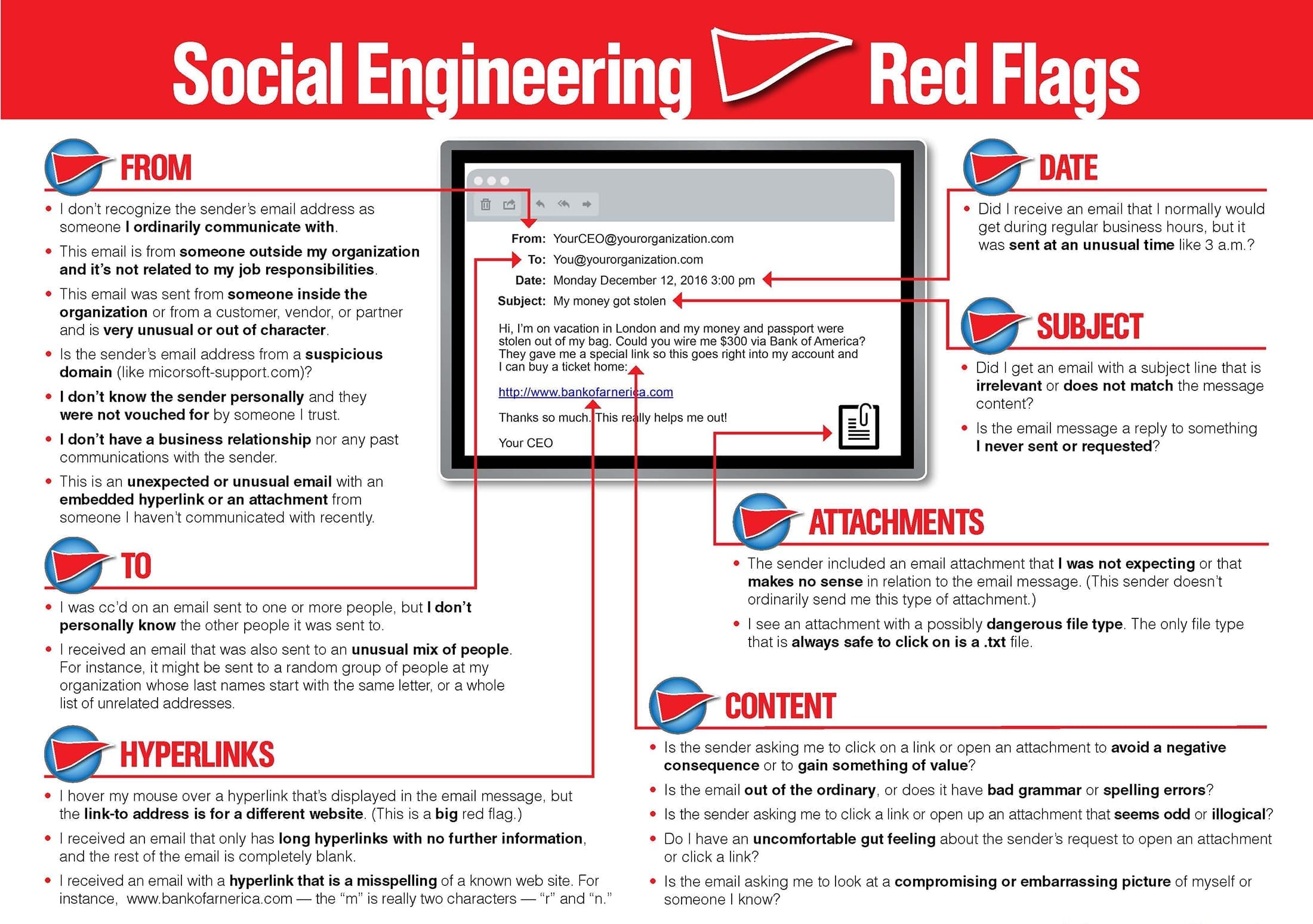
The whole cycle starts with an email one that often talks about the end of a free subscription or being charged for a renewal or the like. This email might not have any links or attachments, but will have a number for the recipient to call.
<sidebar: I’d always thought these types of emails had 1 purpose and that was to scam recipients by getting them to call and then getting them to divulge credit card information or other personal information…my viewpoint was limited .>
When the recipient calls to cancel or dispute the precieved charges they are directed by the ‘call center’ to a website and this website downloads bazarloader malware which can be a carrier for other malicious code like Trojans or Ransomware.

So, I learned something new this week. I’m always amped when I learn something and I usually want to learn more about it. So, I’m doing more deep diving on Bazarloader and to see if there are other similar campaigns.
This whole thing also reinforced thinking outside the box when it comes to attacks. Often times, the simplest objective isn’t the true objective. Why hook a little phish when a marlin is out there like encrypting and ransoming an entire enterprise?
Also long story short, whether it’s a credit card scam or something more malicious, like this: don’t call random numbers in emails.