Spam, Scams, and Being Targeted…
Regardless of whether you are the CEO of a Fortune 500 or a blue-collar worker with hundreds in the bank there is a price on your personal identifiable information (PII). The cost of your information can range from the amount of money you currently have in an account, the amount of credit extended on a card, or the usability of your credentials in escalated attacks. That’s not fear-mongering, it’s a fact. Information is a commodity and either yours and/or the information you hold is worth something. Thankfully, phishing emails can be easily combated with just an increase in situational awareness and following simple rules for emails.
- This means looking at the sender of emails; including matching the sender name and the sender’s email address.
- Being wary of all links and attachments. If the attachment is from a stranger or not expected from the sender err on the side of caution and don’t download it without verifying the sender (not through email).
- Assume links are suspicious. This is just the easiest way to avoid misdirection. If you need to check something out for an account don’t use the email links instead go directly to the site via the browser by typing it in.
References
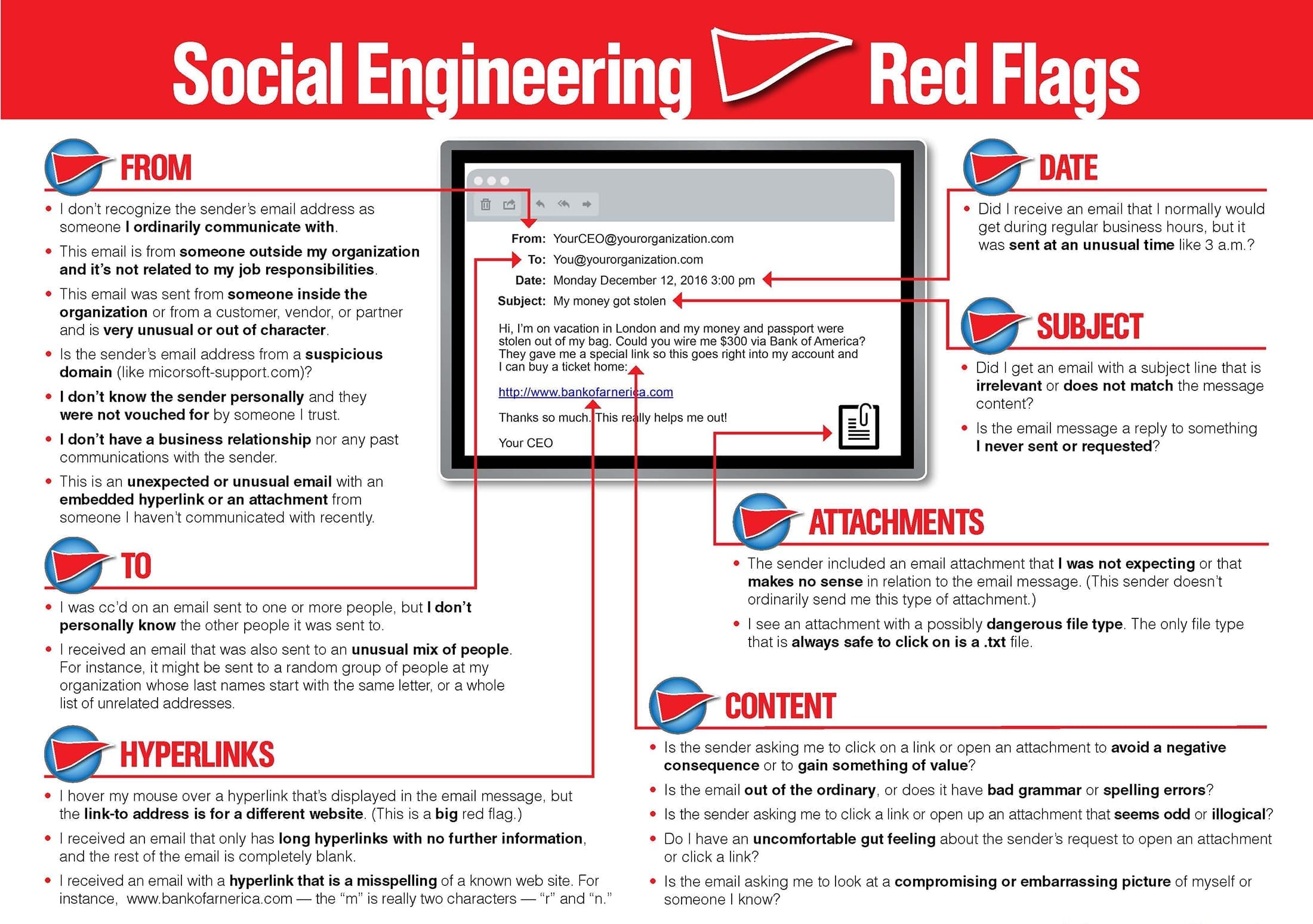
More Examples of PHishing Emails
Glossary
- Phishing – crafted, usually mass-sent emails used to try and garner information from the targets. These are usually not a well crafted, can be automated. Also a broad term that encompasses: spear-phishing and whaling.
- Spear-phishing- An email attack which is targeted to certain people, persons, or groups. These emails will be more well crafted and will try to use public available information to craft the message.
- Whaling-An even more targeted attack than spear-phishing which casts an even smaller “net” targeting CEOs, COOS, and other upper management accounts.
- Social Engineering- Broad term for attacking the “human” element of organizations. This type of attack uses human nature to try and get information or gain access. Phishing falls under social engineering as an attack type.
- Situational Awareness- Practicing calm in the moment in order to analyze environmentally what is occurring.
- Spoof[ing]- Imitation; pretending or portraying to be an entity in which they are not.
