CodeLand – My First Tech Conference
May 2018
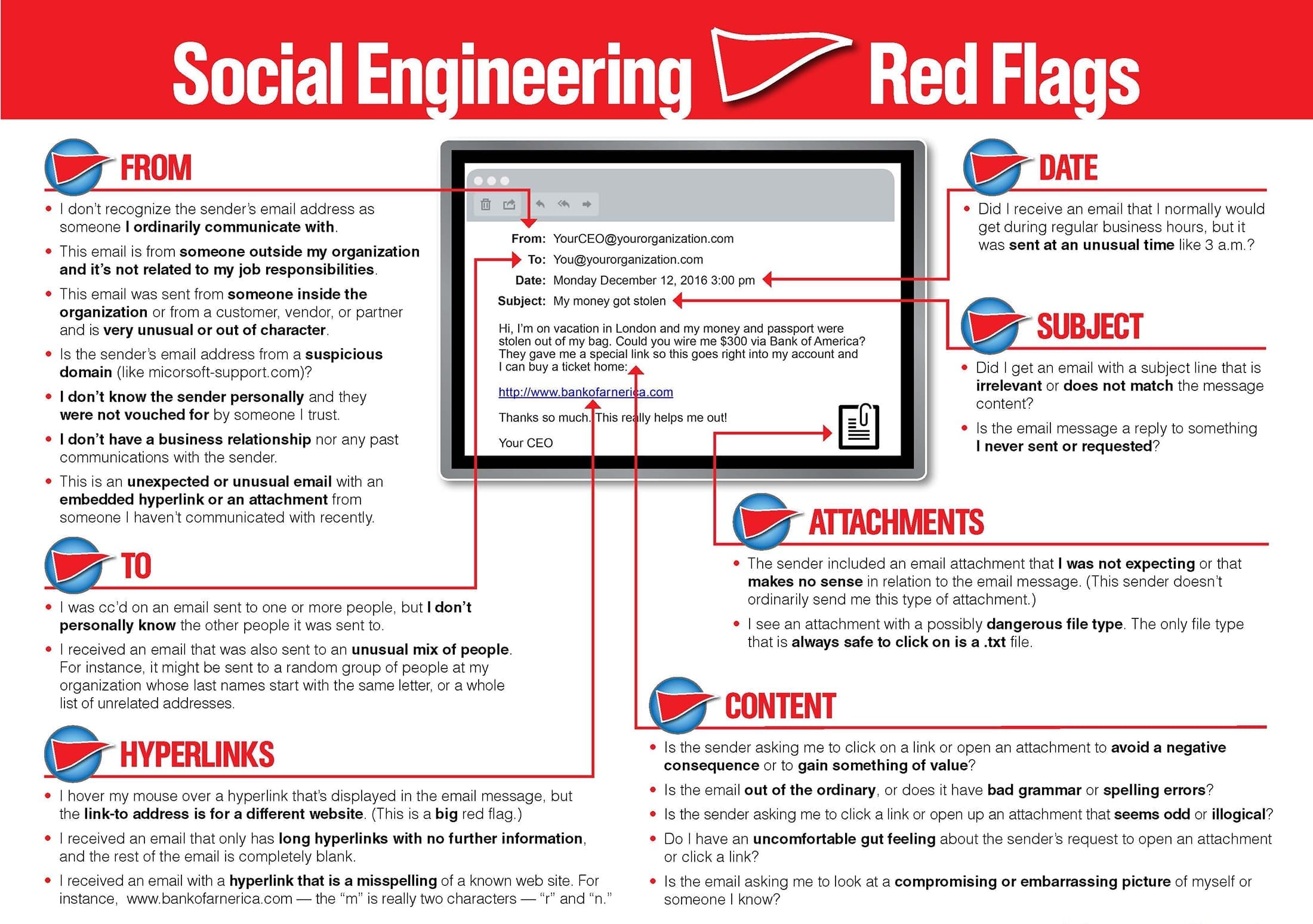
I attended Codeland in May 2018in New York City, New York. This was my first time at a tech conference and I think it was the first or second time they held the conference. It was also my first time in New York City.
Codeland was in a word awesome, because it was approachable. It is put on by Code Newbies and the majority of attendees are newer to coding/programming.
I enjoyed the conference because it didn’t feel like I needed to put on my “professional” face. I could just enjoy being there and listening to the talks and seeing all of the truly awesome ways that people were learning to code and using code in theory projects
If I could have changed 1 thing about the experience it would have been to get to know people there more, but I’m socially awkward on the best day. I also didn’t bring my laptop and that was a mistake.
This year they’re doing it distributed online and I really cannot wait to see how it goes.
Google: Codeland (Distributed) for more details….